SASE – Security as Standard
04/07/2022 by Thomas Dingel and Dr. Branislav Poletanovic

NOTE: This article was initially published in the April 2022 issue of "Swiss IT Magazin". Reuse here as blog post with kind permission from the publishing company
SASE is a software-based framework for network security and is not a concrete product. Much like an airbag in a car, it is part of modern standard equipment, as the experts point out in the large overview.
The future in the automobile will probably look something like this: On a drive from Zurich to Bern, I fell asleep at the wheel. Unusual at first, but I was well rested when I arrived. Current cars brake autonomously in case of danger, and from drivers we can hear: "I didn't brake, but my car was stationary" - even though their attention may not have been 100% on the traffic at that moment. Safety comes as standard with cars today. Whether ABS, airbags, side impact protection or emergency braking assistants. Safety is part of the car design - 'security by construction'.
And with networks? Here it might be, "I didn't brake, neither did the network." With networks, security is still an optional extra and not standard. Much is mapped in a modular way via third-party providers. But it seems a little like the earlier automotive years: the remote-control key, the radio, the GPS system or the rear-view camera - all retrofitted. Not very confidence-inspiring for corporate networks, especially in times when the National Center for Cyber Security (NCSC) reports a steadily increasing number of cyberattacks. So, what do we do?
SASE is Security by Design
In 2019, Gartner proposed Secure Access Service Edge (SASE - pronounced 'sassee'), a framework to solve the problem. Security is a fundamental part of the network design, no longer part of the add-on list or a bolt-on. Analogous to a secure car, a secure network means that network functions and security functions are combined. This makes it clear that SASE is not a product. Safety in cars is also not a product but is individually designed by each manufacturer – size of airbag, control of the ABS, chassis strength – even access is regulated differently. The common denominator is the result: safety in every case.
Zero Trust Paradigm Coupled with Identity
With SASE, the basic security paradigm is "zero trust" – no one has access to the network. Access is granted to those who have an approved identity – cue: personalized car key. This identity guarantees access, but not use. To stay with the automotive analogy: Car opens, but it won't start. What is missing is the context, i.e., what is the user allowed to do in the network or which applications is he allowed to use?
| Security Functions | Network Functions |
|---|---|
| Firewall as a ServiceRemote Access/VPNSecure Web GatewayCloud Access Security BrokerData Loss PreventionZero Trust Network AccessWAF/API ProtectionRemote Browser IsolationEtc. | |
| SD-WANWiFiWAN OptimizationTraffic ShapingPath SelectionGeo RestrictionsLatency OptimizationCDNEtc. | |
| Firewall as a Service | SD-WAN |
| Remote Access/VPN | WiFi |
| Secure Web Gateway | WAN Optimization |
| Cloud Access Security Broker | Traffic Shaping |
| Data Loss Prevention | Path Selection |
| Zero Trust Network Access | Geo Restrictions |
| WAF/API Protection | Latency Optimization |
| Remote Browser Isolation | CDN |
| Etc. | Etc. |
Table 1: Examples of SASE relevant security and network functionalities
Is he allowed to access the cloud service, the financial system or the data center? It is important to understand that each context is subject to a combination of network functionality (e.g., WiFi, path selection – see Table 1) and security features (e.g., Zero Trust Network Access, Secure Web Gateway – see Table 1). This combination looks different for each application scenario. A classic example of such scenarios is, for example, access to the company mails from the airport in the public WLAN or via the LAN in the company headquarters.
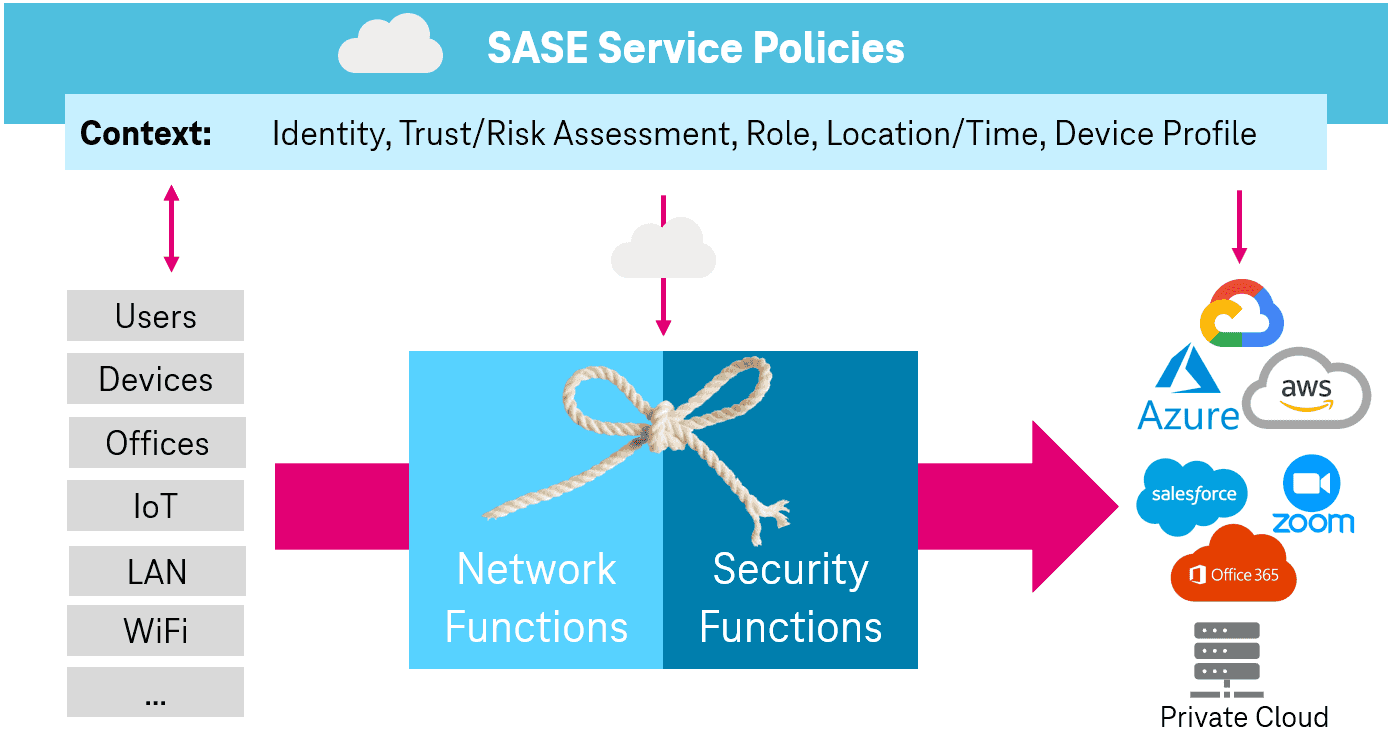
Such application scenarios (identity + context) are summarized in so-called policies. Once defined, policies facilitate the categorization of each access (cf. Fig. 1). SASE can thus be defined as follows:
SASE consolidates all WAN and security functions. Based on application scenarios, security is rolled out as a service via policies to all devices - security is decentralized.
Here we have another aspect of SASE – decentralized security. Two things are essential for this: the policies and fully integrated software across all network components to deliver the policies. The relevance of the software to SASE is further evidence of the paradigm shift in how networking and security are understood – fully integrated, convergent. In the automotive industry, let’s consider Tesla’s approach. Tesla first built the software and the central control unit of the cars. Then they build a sheet metal dress around that control unit. The electrification of classic manufacturers was characterized at the beginning by the fact that for an existing model the electric drive is offered as well, not to say – retrofitted. Tesla's approach, for example, made it possible to raise the battery range limit at short notice during the 2017 Irma storm in the USA – danger recognized, danger averted – thanks to software and decentralized safety. The above-mentioned combination of both ensures seamless distribution to all network nodes (routers, devices or dedicated SASE Points of Production).
Scalability comes as standard – it's not an extra
Another advantage of the decentralized structure of SASE and the software is scalability. Policies are created centrally and rolled out or made accessible to all servers and thus to all devices on the network. In the classic view of an MPLS network or SD-WAN, scalability is not automatic. It is a separate requirement and a challenge to the architecture as well as the network design. This requirement also limits the choice of vendors. Not with SASE – because scalability comes as standard. In other words, the end user is at the edge of the network and is the beneficiary of a service (security). This security is made available to him by many decentralized servers – always and everywhere. This explains the choice of the name SASE: Secure Access as a service of each device (Edge).
SASE is the single pane of glass for networking and security
Gartner's idea about the SASE framework in times of digitalization and software is logical and understandable. But what about the configuration of the individual network, security functions and, for example, policies? The convergent approach of SASE requires bundling everything in one platform. Specifically, a web portal is used, for example, in which the network or even security functions are configured. Profiles are created and assigned to specific users, devices, or roles, for example. SASE is the control center for all services in the network. In this context, SASE is referred to as a "single pane of glass". This enables easy configuration and integration of new application scenarios such as IoT access or remote workers. In Figure 2 we see an example of an employee who is at the airport and wants to access the Salesforce service.
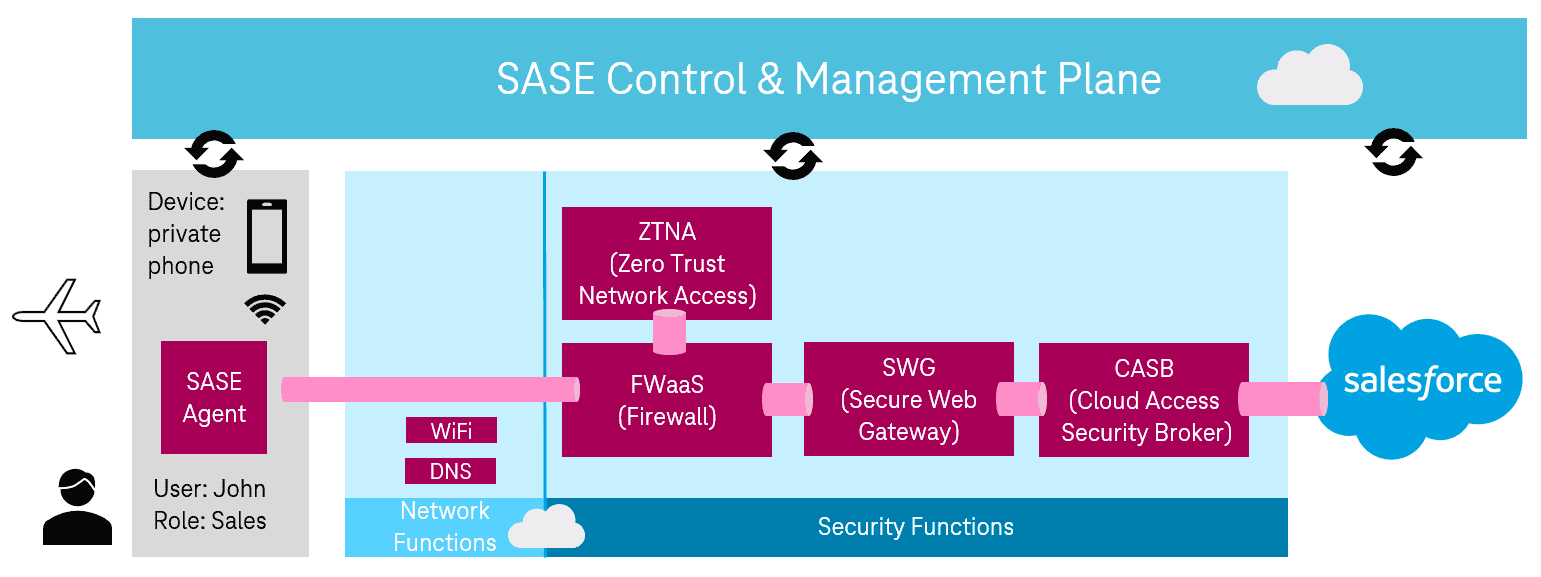
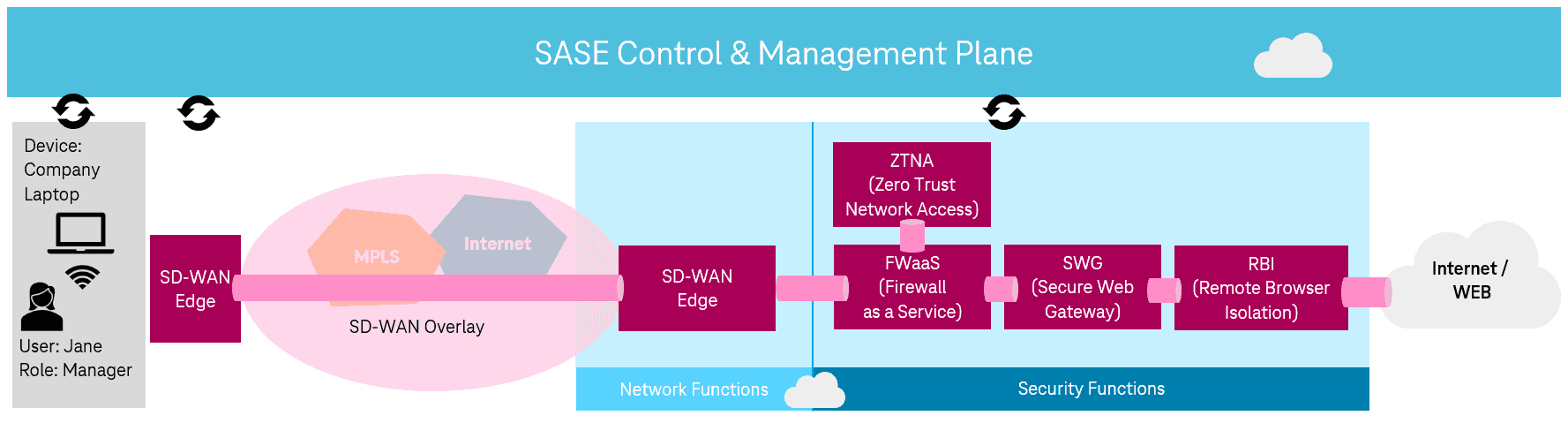
The access is performed from a cell phone. As soon as the access attempt is made, a connection to the SASE Control & Management Plane is established. Identity is used to determine which functions are permitted with that particular identity (e.g. the user Urs Meier) and the context (access from external WiFi network to Salesforce application). For this access, e.g. the network functions, WiFi and DNS are defined and ZTNA, FWaaS, SWG and CASB provide security. Here it is important to see that, as shown in Figure 2, the SASE layer means a network slice end-to-end. All areas (cell phone as device, network/security functions, and the cloud service Salesforce) are in permanent exchange with the SASE layer. Not only is the connection securely established and protected by the ZTNA, FWaaS and SWG services, but even before login, the Cloud Access Security Broker (CASB) checks whether access is permitted for the identity. If the connection were compromised en route, the CASB would deny access as a last resort. To further understand the elegance of SASE, it helps to compare it to another scenario. Figure 3 shows an office worker accessing the Internet. The fundamental difference is that the SD-WAN Edge establishes identity and context. This results in different network and security functions. Recall that all scenarios are pre-defined and pre-configured. This ensures pinpoint and scalable security that is always up to date.
SASE is a journey – the journey is the destination
This sounds simple, but it is precisely the question of specific implementation that Gartner leaves open in its paper. Some vendors pick up partial aspects and thus declare themselves SASE compliant. This is not wrong, but it is not really the whole truth either. SASE is an unavoidable journey; it doesn't matter where the journey begins, whether with MPLS or SD-WAN. By its very nature, the gap between SD-WAN and SASE is smaller, as SD-WAN already puts software at the center of network functionality. Here it should be clearly pointed out again that SASE is not security from the cloud. If SD-WAN is supplemented by security functions from the cloud, this is in no case SASE!
SASE doesn't affect some companies – it affects everyone!
Now we know that the journey must begin – but who should travel and when? General guiding principle: if most of the data or services are outside the enterprise, the journey should begin as soon as possible. The size of the company does not matter – there is no exclusivity for large companies. Security is key – small cars have airbags too. Once cloud services like O365, AWS, Google, etc. are used, you are increasing the opportunities for attack. It's hard to imagine what happens when mails are intercepted, patents are stolen, or production must be stopped. Hackers are constantly changing their attack targets, patterns, and strategies. SASE makes it possible to react to these threats in near real time. Any change, e.g., in security policies, can be applied immediately. The software is the key here. The full integration of network functions and security functions, rolled out in a decentralized manner, provided as a service and also scalable, is the indispensable future of networks. Otherwise, companies will not be able to fend off the increasing threats to their networks and the associated IT landscape.
How do you find the right SASE provider? The market is currently in a state of flux. New security functionalities, concepts and providers are continuously being added. And this makes selection difficult. For each provider, his own solution is the best, or as the saying goes: “To him who has a hammer, everything looks like a nail.” It is better to use consultants who have an overview of the market as well as practical experience with the solutions. Experience is important because it is in the technical details that differences lie. A detailed examination of the requirements must be made and then the appropriate solution selected.
Finally, a look at the costs. The myth persists that immediate cost savings can be achieved by implementing SD-WAN and SASE. It is important to understand: that SASE is a framework which elegantly and with scalability, links networking and security on a software basis. As such, it offers a more powerful approach to security at a comparable cost. Monthly cancellable licensing models from various vendors provide ample room for trial and error.
This flexibility is an omen of Software Defined Anything (SD-X), which emphasizes networks as a service – easy and fast ordering, reordering and overview of services used.
Conclusion: SASE is a framework that combines network and security functions on a software basis in a fully convergent and scalable way. It is the future that starts today.

